HANDBOOK AS-805-A REVISION
Application Information Security Assurance Process
Handbook AS-805-A, Application Information Security Assurance (ISA) Process, is revised as follows to streamline the process.
We will incorporate these revisions into the next online update of Handbook AS-805-A available on the PolicyNet Web site:
• Go to http://blue.usps.gov.
• Under "Essential Links" in the left-hand column, click on References.
• Under "References" in the right-hand column, under "Policies," click on PolicyNet.
• Then click on HBKs.
(The direct URL for the Postal ServiceTM PolicyNet Web site is http://blue.usps.gov/cpim.)
Handbook AS-805-A, Application Information Security Assurance (ISA) Process
* * * * *
2 Roles and Responsibilities
* * * * *
2-2 Vice President, Chief Technology Officer
[Add a sentence to the end of the section to read as follows:]
***The VP/CTO has delegated this responsibility to the applicable manager, business systems portfolio (portfolio manager).
2-3 Manager, Corporate Information Security Office
The manager, Corporate Information Security Office (CISO), is responsible for the following:
* * * * *
[Revise item e to read as follows:]
e. Reviewing the ISA documentation package and accrediting the application.
2-4 Vice Presidents of Functional Business Areas
Vice presidents of functional business areas are responsible for the following:
* * * * *
[Add a sentence to the end of item b to read as follows:]
b. ***The vice presidents of functional business areas have delegated this responsibility to the applicable executive sponsor.
* * * * *
2-5 Executive Sponsors
***Executive sponsors are responsible for the following:
* * * * *
[Revise item c to read as follows:]
c. Appointing, if desired, an information systems security representative (ISSR) to serve as a development team point of contact to perform security-related activities.
* * * * *
[Add new item f to read as follows:]
f. Working jointly with the portfolio manager to review the ISA documentation package and accept the application for production or return the application to the applicable lifecycle phase for rework.
2-6 Portfolio Managers
Portfolio managers are responsible for the following:
* * * * *
[Revise item c and add new items d and e to read as follows:]
c. Appointing, if desired, an information systems security representative (ISSR) to serve as a development team point of contact to perform security-related activities.
d. Reviewing the ISA documentation package and completing a risk mitigation plan for risks identified as High or Medium.
e. Working jointly with the executive sponsor to review the ISA documentation package and accept the application for production or return the application to the applicable life cycle phase for rework.
* * * * *
2-9 Certifier
[Revise text to read as follows:]
The manager, Information Security Assurance, who is appointed by the CISO, functions as the certifier and is responsible for the following:
a. Reviewing the ISA evaluation report and the supporting ISA documentation package.
b. Escalating security concerns or preparing and signing a certification letter.
c. Forwarding the certification letter and ISA documentation package to the portfolio manager.
[Revise the title and text of 2-10 to read as follows:]
2-10 Accreditor
The manager, Corporate Information Security Office, functions as the accreditor and is responsible for the following:
a Reviewing the risk mitigation plan and supporting ISA documentation package together with business requirements and relevant Postal Service issues.
b. Escalating security concerns or preparing and signing an accreditation letter that makes one of the following recommendations: accepting the application with its existing information security controls, requiring additional security controls with a timeline to implement, or deferring deployment until information security requirements can be met.
c. Forwarding the accreditation letter and ISA documentation package to the portfolio manager and executive sponsor.
2-11 Information Systems Security Officers
Information systems security officers (ISSOs) are responsible for the following:
* * * * *
[Revise items e and f to read as follows:]
e. Preparing the ISA evaluation report.
f. Forwarding the ISA evaluation report and supporting ISA documentation package to the certifier.
2-12 Information Systems Security Representatives
***Responsibilities may include the following:
* * * * *
[Revise item b to read as follows:]
b. Notifying the executive sponsor, portfolio manager, and ISSO of any additional security risks or concerns that emerge during development, acquisition, or integration of the application.
* * * * *
2-15 Disaster Recovery Services
Disaster Recovery Services (DRS) is responsible for the following:
* * * * *
[Add item d to read as follows:]
d. Supporting the exercise of the ADRP.
* * * * *
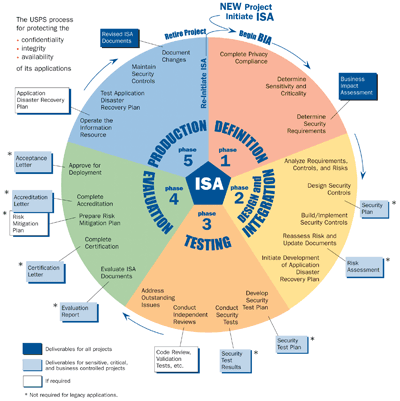
3 Overview of ISA
* * * * *
3-2 What ISA Applies To
[Revise the first sentence to read as follows:]
The ISA applies to all applications (new, legacy, small, or field) sponsored by, developed for, or maintained or operated on behalf of the Postal Service, whether or not they are located at a Postal Service facility.***
3-2.1 For New Applications
* * * * *
[Add new 3-2.1.3 to read as follows:]
3-2.1.3 Field Applications
Field applications are not national applications and are hosted on a server located in the Field Information Systems Server Farm at Eagan. Field applications are classified as noncritical and can never be critical or business-controlled criticality. Field applications facilitate the completion of one or more specific tasks, establish a unique session with each user, and allow users to make permanent changes to stored data. A Field Application BIA Questionnaire is used to determine privacy, sensitivity, and information security requirements.
[Revise title and text of 3-2.2 to read as follows:]
3-2.2 Legacy Applications
Legacy applications are applications that have been in production prior to January 1, 2003. Most of these applications are processed on mainframes.
3-3 Frequency of ISA
[Revise text to read every 5 years instead of every 3 years as follows:]
The ISA is performed at least every 5 years on an application following its last certification and accreditation or sooner if the application undergoes significant change. See Chapter 6, Re-Initiating the ISA, for specific reasons.
* * * * *
Exhibit 3-1
ISA Phases and Major Deliverables
[Revise Exhibit 3-1 as follows:]
4 The ISA Process
* * * * *
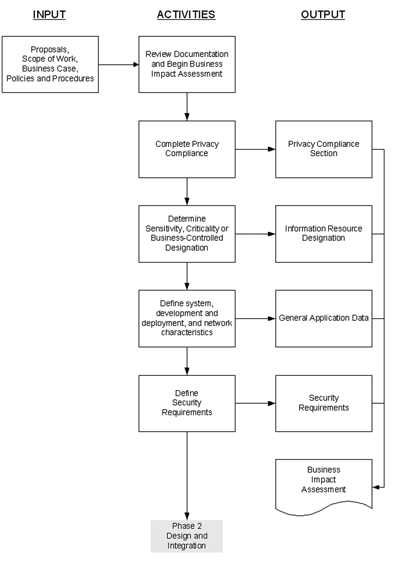
4-1 Phase 1 - Definition
4-1.1 Objectives
Phase 1 objectives are as follows:
* * * * *
[Revise item b of this section to read as follows:]
b. Determining the sensitivity and criticality of the application.
* * * * *
4-1.3 Roles and Responsibilities
[Revise the third row of this table to read as follows:]
| Roles |
Responsibilities |
| ISSR |
Supports executive sponsor and portfolio manager as requested. |
4-1.4 Activities
* * * * *
4-1.4.3 Complete Application Business Impact Assessment
[Revise text to read as follows:]
The ISSO coordinates the completion of the application BIA, which includes the following steps:
a. Completing the privacy section.
b. Determining sensitivity and criticality.
c. Determining security requirements.
d. Signing Acceptance of Responsibility and Verification sections of BIA. (The portfolio manager as executive sponsor designee, privacy official, and ISSO sign.)
Note: Some applications are developed under the direction of one executive sponsor in one organization and transferred to an executive sponsor in another organization for Phase 5 of the ISA process (Production).
Template and instructions for completing the applications are available on the Information Technology Web site at http://cto.usps.gov; select Corporate Information Security from the Support drop-down menu, then Information Security Assurance, then ISA Templates.
* * * * *
[Add new 4-1.5.3 to read as follows:]
4-1.5.2 Applications Designated as Legacy
Legacy applications utilizing credit card transactions need to complete a full ISA.
For other legacy applications, perform a BIA, verify platform hardening, conduct a vulnerability scan, and complete an ADRP if the application was determined to be critical or business-controlled criticality.
Exhibit 4-1
Phase 1, Definition
[Revise Exhibit 4-1 as follows:]
4-2 Phase 2 - Design and Integration
* * * * *
4-2.3 Roles and Responsibilities
[Revise the fourth row of this table to read as follows:]
| Roles |
Responsibilities |
| ISSR |
Supports executive sponsor and portfolio manager as requested. |
* * * * *
4-2.4 Activities
* * * * *
4-2.4.2 Assess Risks
* * * * *
4-2.4.2.1 Application Risk Assessment and Abbreviated Application Risk Assessment
* * * * *
[Revise the third row of this table and add a fourth row to read as follows:]
| If the application is... |
The required activity is... |
| Small and suitable for rapid security review. |
Abbreviated application risk assessment. |
| Legacy or field |
Not applicable. |
* * * * *
4-2.4.2.1.2 Application Risk Assessment Roles and Responsibilities
[Revise the first and third rows of this table to read as follows:]
| Roles |
Responsibilities |
| Executive sponsor |
Ensures completion of application risk assessment for all critical and sensitive applications and abbreviated application risk assessment for all business-controlled sensitivity, business-controlled criticality, and small applications suitable for rapid security review process under their purview.
Provides personnel and financial resources to support risk assessment activities. |
| ISSR |
Supports executive sponsor and portfolio manager as requested. |
* * * * *
4-2.4.6 Develop Application Security Plan
4-2.4.6.1 General
* * * * *
[Revise the third row of the table to read as follows:]
| If the application is... |
The requirement is... |
| Legacy, small, or field |
Not applicable. |
* * * * *
4-2.4.6.3 Application Security Plan Roles and Responsibilities
[Revise the third row of this table to read as follows:]
| Roles |
Responsibilities |
| ISSR |
Supports executive sponsor and portfolio manager as requested. |
* * * * *
4-2.4.10 Initiate Application Contingency Planning
[Revise text to read as follows:]
If Phase 1 determines that contingency planning is required based on the criticality determination, it should be initiated at this stage. Contingency planning continues throughout the life cycle of the application.
* * * * *
[Revise title of 4-2.4.10.1 to read as follows:]
4-2.4.10.1 Application Contingency Planning Roles and Responsibilities
[Revise the first and third rows of the table to read as follows:]
| Roles |
Responsibilities |
| Executive sponsor |
Consults with the DRS on the ADRP and the RTO.
Coordinates with other managers in planning contingency planning activities.
Develops and maintains the ADRP.
Funds application contingency planning activities. |
| ISSR |
Supports executive sponsor and portfolio manager as requested. |
* * * * *
4-3 Phase 3 - Testing
* * * * *
4-3.3 Roles and Responsibilities
[Revise the third row of this table to read as follows:]
| Roles |
Responsibilities |
| ISSR |
Supports executive sponsor and portfolio manager as requested. |
* * * * *
4-3.4 Activities
* * * * *
4-3.4.4 Conduct Security Code Review
[Add a new sentence as the first sentence of this section to read as follows:]
Code reviews are generally not required for legacy applications.***
* * * * *
[Renumber current 4-3.4.5 and 4-3.4.6 as new 4-3.4.7 and 4-3.4.8. Add new 4-3.4.5 and 4-3.4.6 to read as follows:]
4-3.4.5 Harden Platform
All information resources (servers) must be hardened to Postal Service standards.
4-3.4.6 Conduct Vulnerability Scans
Vulnerability scans are recommended for all applications and are required for the following applications:
a. Legacy applications.
b. Externally facing applications.
c. Applications utilizing credit card transactions.
4-4 Phase 4 - Evaluation
* * * * *
4-4.3 Roles and Responsibilities
[Change the table to read as follows:]
| Roles |
Responsibilities |
| ISSO |
Evaluates ISA documentation, prepares an ISA evaluation report that details the findings, makes the decision to escalate security concerns, or forwards the ISA evaluation report and the ISA documentation package to the certifier. |
| Certifier (manager, ISA process) |
Reviews the ISA evaluation report and ISA documentation package, makes the decision to escalate security concerns or certifies the application by preparing and signing a certification letter, and forwards the certification letter and ISA documentation package to the portfolio manager. |
| Portfolio manager |
Analyzes ISA and business documentation, makes the decision to escalate security concerns or prepares a risk mitigation plan which addresses High and Medium risks, and forwards the risk mitigation plan and ISA documentation package to the accreditor. |
| Accreditor (manager, CISO) |
Analyzes ISA and business documentation, makes the decision to escalate security concerns or prepares an accreditation letter, and forwards the accreditation letter and ISA documentation package to the executive sponsor and portfolio manager. |
| Executive sponsor and portfolio manager as agents of the VP functional business area and VP/CTO |
Jointly review ISA and business documentation and make the decision to return the application to the applicable ISA phase for rework or to deploy it into the production environment by preparing and signing an acceptance letter. |
| Executive sponsor |
Ensures completion of ISA process and provides personnel and financial resources for correcting deficiencies. |
| ISSR |
Supports executive sponsor and portfolio manager as requested to correct deficiencies. |
| Other stakeholders |
Participate by responding on outstanding issues or providing advisory support. |
4-4.4 Activities
* * * * *
[Revise title and text of 4-4.4.3 to read as follows:]
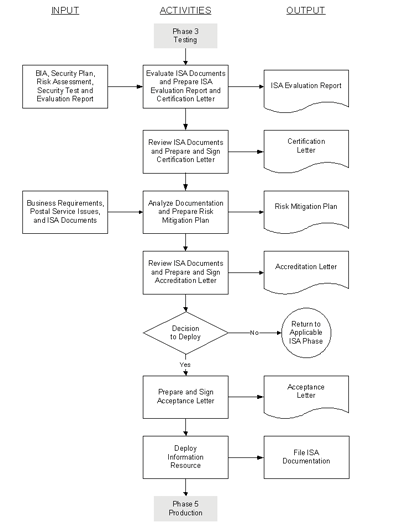
4-4.4.3 Escalate Security Concerns or Forward ISA Package
Upon completion of the ISA evaluation report, the ISSO escalates security concerns or forwards the ISA evaluation report and supporting documentation to the certifier (manager, ISA process) for review.
4-4.4.4 Escalate Security Concerns or Certify Application
[Revise text to read as follows:]
The certifier (manager, ISA process) reviews the ISA evaluation report and the supporting ISA documentation package, escalates security concerns or prepares and signs a certification letter, and forwards the certification letter and ISA documentation package to the portfolio manager.
[Renumber current 4-4.4.5 and 4-4.4.6 as new 4-4.4.6 and 4-4.4.7. Add new 4-4.4.5 to read as follows:]
4-4.4.5 Escalate Security Concerns or Prepare Risk Mitigation Plan
The portfolio manager reviews the certification letter and the supporting ISA and business documentation, escalates security concerns or prepares a risk mitigation plan for any residual risks rated as Medium or High, recommending whether the risks should be accepted, transferred, or further mitigated. The portfolio manager then forwards the risk mitigation plan and ISA documentation package to the accreditor.
4-4.4.6 Escalate Security Concerns or Accredit Application
[Revise text to read as follows:]
The accreditor (manager, CISO) reviews the risk mitigation plan and the supporting ISA documentation, escalates security concerns or prepares and signs an accreditation letter, and forwards the accreditation letter and final ISA documentation package to the executive sponsor and portfolio manager.
4-4.4.7 Make Decision to Deploy (or Continue to Deploy) or Return for Rework
[Revise text to read as follows:]
The executive sponsor and portfolio manager review the accreditation letter, risk mitigation plan, and supporting ISA documentation package. They will issue a joint decision on whether to accept the residual risk and deploy the application and with what restrictions, if any. If they decide not to approve deployment, they will indicate the ISA Phase to return to for rework. If they decide to approve and deploy, they will prepare and sign an acceptance letter.
Exhibit 4-4
Phase 4, Evaluation
[Revise Exhibit 4-4 to read as follows:]
4-5 Phase 5 - Production
* * * * *
4-5.3 Roles and Responsibilities
[Revise the third row of the table to read as follows:]
| Roles |
Responsibilities |
| ISSR |
Supports executive sponsor and portfolio manager as requested. |
4-5.4 Activities
* * * * *
4-5.4.2 Re-Initiate ISA as Required
[Revise the first sentence of this section to read every 5 years instead of every 3 years as follows:]
Re-initiate the ISA every 5 years or if there is a significant change to the application.***
* * * * *
4-5.4.3 Reassess Risks
[Revise the first sentence of this section to read every 5 years instead of every 3 years as follows:]
Reassess risk every 5 years and whenever major changes are made to the application, a serious breach occurs, or audit findings regarding security are issued.***
* * * * *
Exhibit 4a ISA Templates
[Revise Exhibit 4a as follows:]
Exhibit 4a
ISA Templates
| Template Name |
Applicability |
Purpose |
| ISA Status Tracking Sheet |
Optional use. |
To record responsible office and the schedule of completion for each ISA product. |
| Business Impact Assessment |
For all applications. |
To determine level of sensitivity and criticality and the information security requirements for an application. |
Application Security Plan
(Abbreviated Application Security Plan) |
Full version is for sensitive and critical applications.
Abbreviated version is for business-controlled applications.
Neither plan is required for legacy, small, or field applications. |
To create a blueprint for designing, building, and maintaining an application that can be defended against threats and intruders, both internal and external. |
Application Risk Assessment
(Abbreviated Application Risk Assessment) |
Full version is for sensitive and critical applications.
Abbreviated version is for business-controlled and small applications.
Neither assessment is required for legacy or field applications |
To identify assets at risk and their value and weaknesses and vulnerabilities, evaluate threats and vulnerabilities to determine risks, identify safeguards, analyze costs and benefits of safeguards, and complete the risk assessment report. |
| Application Disaster Recovery Plan (ADRP) |
For critical and business-controlled criticality applications including legacy and small applications.
Not required for field applications.
(ADRP templates may be found at the IT Security Web site [http://it/security]; click Information Security Assurance, then ISA Templates.) |
To provide cost-effective recovery of an application and protection of assets in the event of a significant interruption of computing services. |
| Application Security Test and Evaluation Plan |
For sensitive, critical, and business-controlled applications.
Not required for legacy, small, or field applications. |
To evaluate technical/nontechnical security controls/safeguards to establish extent to which an application meets security requirements. |
| Independent Risk Assessment Report |
May be recommended if system is publicly accessible; developed, hosted, managed primarily by non-Postal Service personnel; highly visible or has high impact. May be required at any time by VP/CTO; Mgr., CISO; or VP of the functional business area. |
To provide a standard report format to document results of independent risk assessment, i.e., one conducted by an entity outside the development organization. |
| ISA Evaluation Report |
For sensitive, critical, business-controlled, and small applications. |
To document the ISSO's evaluation of technical and nontechnical security features and other safeguards to establish extent to which an application meets security requirements. |
| Certification Letter |
For sensitive, critical, business-controlled, and small applications. |
For certifier to recommend approval for an application to be deployed if the "High" and "Medium" residual risks are mitigated. |
| Risk Mitigation Plan |
For sensitive, critical, business-controlled, and small applications where residual risk is "High" or "Medium". |
For the portfolio manager to describe the plan to mitigate the "High" or "Medium" residual risks. |
| Accreditation Letter |
For sensitive, critical, and business-controlled applications.
Not required for legacy or field applications. |
For accreditor to recommend approval for an application to operate in given operational concept and environment at a documented level of residual risk. |
| Acceptance Letter |
For sensitive, critical, and business-controlled applications.
Not required for legacy, small, or field applications. |
For executive sponsor and portfolio manager as agents of the vice president of the functional business area and VP/CTO to jointly decide, in writing, whether to accept the residual risk and approve the application deployment. |
continue > |
