|
HANDBOOK AS-873 REVISION
Telecommunications Services
Effective immediately, Handbook AS-873,
Telecommunications Services, is revised to update the policies
and requirements related to personal digital assistant (PDA) devices used
in the Postal ServiceTM.
We will incorporate these revisions
into the next online update of Handbook AS-873 accessible on the Postal
Service PolicyNet Web site:
• Go to http://blue.usps.gov.
• Under "Essential Links"
in the left-hand column, click on References.
• Under "References"
in the right-hand column, under "Policies," click on PolicyNet.
• Then click on HBKs.
(The direct URL for the Postal Service
PolicyNet Web site is http://blue.usps.gov/cpim.)
Handbook AS-873, Telecommunications Services
* * * * *
9 Wireless Communications
* * * * *
[Revise title and text to read
as follows:]
9-4 Wireless Data Communications
9-4.1 Policy
The Blackberry is the Postal Service
standard, and the only personal digital assistant (PDA) device supported
by Information Technology (IT). Future technology enhancements may change
this standard; however, the policies and procedures provided in this instruction
will apply to all replacements and any additional PDA devices that become
part of the Postal Service infrastructure.
9-4.2 Applicability
The policy and procedures for provisioning
and supporting all personal digital assistant devices apply to all levels
of the Postal Service, regardless of the source of funding.
9-4.3 Service Options
Data Services
a. Data services consist
of e-mail and PIN-to-PIN (Blackberry to Blackberry) communications and
are required for all Blackberry hardware purchases.
b. Responsibility for funding
the recurring monthly costs associated with these services is outlined
below.
c. Approving PCES managers
should carefully consider the responsibilities described below when approving
the initial Blackberry device purchase.
Voice Services
a. Voice services will
not be activated without the PCES manager's approval.
b. Voice will not be activated
unless a calling plan has been selected.
c. All voice services are
funded locally.
d. To have this voice service
activated, you must turn in your Postal Service-distributed mobile phone
and pager (if one was in use) prior to Blackberry activation.
Service Changes
Contact the service provider directly
for all subsequent changes in service.
User Information Changes
Update user information changes in
the eAccess system.
9-4.4 Funding
General
All managers are expected to exercise
fiscal responsibility in approving new Blackberry devices (and all other
nonstandard PDAs for authorized Blackberry users), replacing cellular
phones, and implementing the above guidelines in their entirety.
For Officers and PCES Managers
a. Information Technology
(IT) will fund the initial purchase of PDAs for officers and PCES managers.
This funding includes a one-time setup charge and recurring monthly charges
for data services. IT will also fund and manage all corporate-wide upgrades.
b. Area and district offices
will fund locally initiated upgrades, replacement of damaged devices,
and voice- service costs.
For Field IT Staff (District
& BMC IS and Area ITPC)
IT will fund devices for the field
IT staff and the recurring voice-service costs, as well as all upgrades
and replacement costs.
For EAS Positions
PCES managers will fund PDAs for their
respective EAS employees.
For Contract Employees
PDAs for contract employees must be
approved and funded by their PCES manager. Their job duties must require
after-hours communications, availability, or immediate communications
capability to support the function of the organization.
9-4.5 Eligibility
General
Managers should consider these guidelines
when determining the need to provide PDAs to noncritical positions:
a. An employee's job duties
require after-hours communications to support the function of that employee's
organization.
b. An employee's job duties
require immediate communications to support the function of that employee's
organization.
Contract Employees
Contract employee job duties must require
after-hours communications, availability, or immediate communications
capability to support the function of the organization.
FLSA Non-Exempt and Bargaining
Unit Employees
FLSA non-exempt and bargaining unit
employees are not eligible to receive PDAs.
9-4.6 Provisioning PDAs/Blackberry
Outlook Account Requirement
Users must have an ACE/Exchange (Outlook)
account before a connection will be configured. No hardware or service
will be provided for users who do not have an active Outlook account.
For New Service
To establish a new Blackberry device,
complete the following steps:
1. Prepare and process
an eBuy request, and obtain approval from your PCES manager.
• Cost and plan information is
in the Cost&Rates.xls file located at: http://it-blackberry.
• The GL Account number is 54405.
2. Go to eAccess, request
access, and choose ACE Blackberry at the "application requested"
prompt. Complete all information requested and obtain approval. (The devices
will be shipped to the requestor's address specified on the eBuy.)
3. Complete the self-activation
instructions detailed at: http://it-blackberry.
Note: If
you need help in activating your device, contact the IT Corporate Help
Desk at 800-USPS-HELP (800-877-7435). When prompted by the Integrated
Voice Response (IVR) system, say "BlackBerry."
9-4.7 Help Desk Support
Account Setup, Transfer, Problem
Resolution
Contact the IT Corporate Help Desk
at 800-USPS-HELP (800-877-7435). When prompted, say "BlackBerry."
Note:
For lost or stolen devices, contact the IT Help Desk immediately for assistance
in disabling the device. After the device is disabled and it is reasonably
determined that it is not recoverable, a replacement device can be obtained
through the standard order process described here.
Repair and Replacement Service
Contact the IT Corporate Help Desk.
For a hardware problem and/or broken device, the Blackberry may be replaced
through warranty. See the process at:
http://it-blackberry.
9-4.8 Inventory Tracking
All PDAs must be inventoried and tracked
using the national Asset Information Management System (AIMS).
Headquarters Computing Infrastructure
Services (HCIS), IT
HCIS is responsible for entering and
tracking (in AIMS) those PDAs assigned to Headquarters-domiciled employees.
Area, District, and BMC IT
Managers
Area, district, and BMC managers are
responsible for entering and tracking PDAs issued to their field employees.
9-4.10 What To Do When a Position
or Job Duty Changes
General
Because devices are assigned according
to position, job duties, and/or responsibilities, you must do the following
when there is a change:
a. When a position is cancelled,
return the device to the address
below for reissue or inventory surplus as appropriate.
WIRELESS AND PDA NATIONAL PROGRAM OFFICE
475 L'ENFANT PLAZA SW ROOM 2P659
WASHINGTON DC 20260-0651
b. When an employee leaves
a position, return the device to
the Wireless and PDA National Program Office for configuring and reissue
to the new employee for that position.
eAccess Update
All transfers of Blackberry devices
from one person to another must be supported by an update to the eAccess
system. For contractors, the contracting officer representative (COR)
must revoke access account; for postal employees, the PCES manager is
responsible for revoking the account.
* * * * *
— Headquarters Computing
Infrastructure Services, Information Technology, 9-29-05
HANDBOOK AS-805 REVISION
Information Security
Effective September 29, 2005, Handbook
AS-805, Information Security, is revised as follows to address:
• Gaining access to controlled
areas.
• Updating the facility business
continuance management planning section.
• Registering applications in
eAccess.
• Implementing an acceptance of
responsibility letter for documented vulnerabilities that will not be
mitigated.
• Implementing patch management
of information resources.
• Updating Appendix A.
• Updating Appendix B.
We will incorporate these revisions
into the next online update of Handbook AS-805 available on the Postal
ServiceTM PolicyNet Web site:
• Go to http://blue.usps.gov.
• Under "Essential Links"
in the left-hand column, click on References.
• Under "References"
in the right-hand column, under "Policies," click on PolicyNet.
• Then click on HBKs.
(The direct URL for the Postal Service
PolicyNet Web site is http://blue.usps.gov/cpim.)
Handbook AS-805, Information Security
* * * * *
7 Physical and Environmental
Security
* * * * *
7-2 Roles and Responsibilities
* * * * *
7-2.6 All Personnel
All personnel are responsible for the
following:
* * * * *
[Reletter current items b through
e as new items d through g. Add new items b and c to read as follows:]
b. Always using their physical
and technology electromechanical access control identification badge or
device to gain entrance to a controlled area.
c. Ensuring no one tailgates
into a controlled area on their badge.
* * * * *
7-3 Facility Security
* * * * *
7-3.1 Physical Access Controls
* * * * *
7-3.1.3
Access to Controlled Areas
[Revise 7-3.1.3 to read as follows:]
Access to controlled areas is restricted
to personnel whose duties require access to such facilities and who possess
appropriate security clearances. Access to controlled areas must be authorized
and tailgating is not allowed.
Access to controlled areas must be
controlled by electromechanical means. Personnel authorized access to
the controlled areas must always use their physical and technology electromechanical
access control identification badge or device to gain entrance to the
controlled area. It is their responsibility to ensure no one tailgates
on their badge.
Personnel without an authorized physical
and technology electromechanical access control identification badge or
device must be escorted by authorized personnel while in the controlled
area.
* * * * *
[Revise the title and text of 7-3.4
to read as follows:]
7-3.4 Facility Business Continuance
Management Planning
Physical security requirements must
be included in facility business continuance management (BCM) planning
to ensure the appropriate protection of information resources following
a catastrophic event (see Chapter 12).
* * * * *
8 System, Applications, and
Product Development
* * * * *
8-2 Roles and Responsibilities
* * * * *
8-2.6 Portfolio Managers
Portfolio managers are responsible
for the following:
* * * * *
[Reletter current items e through
g as new items f through h. Add new item e to read as follows:]
e. If a documented vulnerability
will not be mitigated, preparing and signing an acceptance of responsibility
letter as part of the ISA process.
* * * * *
Exhibit 8.2 System,
Application, and Product Development Responsibilities
[Revise Exhibit 8.2 as follows:]
| Activity
|
Executive
Sponsors |
Portfolio
Managers |
Project
Managers |
ISSOs
|
ISSRs
|
Certifier1
|
Accreditor2
|
| Initiate ISA &
conduct BIA. |
X/F |
C |
P |
P |
P |
blank |
blank |
| Conduct risk assessment.
|
X/F |
C |
P |
P |
P |
blank |
blank |
| Identify security
controls. |
X/F |
C |
P |
C |
P |
blank |
blank |
| Develop security
plan & develop/acquire security controls. |
X/F |
C |
P |
C |
P |
blank |
blank |
| Develop SOPs, service
level & trading partner agreements. |
X/F |
C |
P |
C |
P |
blank |
blank |
| Develop security
test plan. |
X/F |
C |
P |
C |
P |
blank |
blank |
| Conduct security
testing & document results. |
X/F |
C |
X |
C |
P |
blank |
blank |
| Conduct independent
reviews as required. |
X/F |
C |
P |
C |
P |
blank |
blank |
| Develop ISA package.
|
X/F |
C |
P |
P |
X |
blank |
blank |
| Review ISA package
& write evaluation report. |
blank |
blank |
blank |
X |
blank |
blank |
blank |
| Certify application.
|
F |
blank |
blank |
blank |
blank |
X |
blank |
| Prepare risk mitigation
plan and accept responsibility for documented vulnerabilities
|
F |
X |
blank |
C |
blank |
blank |
blank |
| Accredit application.
|
F |
blank |
blank |
blank |
blank |
blank |
X |
| Accept risk &
approve for deployment. |
X |
X |
C |
C |
blank |
C |
C |
| Develop and test
ADRP & FR Plan |
X/F |
C |
P |
C |
P |
blank |
blank |
| Follow security-related
plans, periodically review, test and audit. |
X/F |
C |
P |
C |
P |
blank |
blank |
| Reassess risks &
upgrade controls, update security-related documents. |
X/F |
C |
P |
C |
P |
blank |
blank |
| Re-initiate ISA.
|
X/F |
C |
P |
X |
P |
blank |
X |
| Retire application.
|
X/F |
C |
P |
C |
P |
blank |
blank |
1 Manager,
ISA Process.
2 Manager, Corporate Information Security Office
(CISO)
X = Responsible for accomplishment
F = Responsible for funding
P = Participant
C = Consulting support as required |
Other organizations and managers
responsible for system, application, and product development include:
chief inspector; inspector general;
chief privacy officer; contracting officers and general counsel; and business
partners (see Appendix A, Consolidated Roles and Responsibilities,
for details).
* * * * *
8-6 Application Information
Security Assurance Phases
* * * * *
8-6.1 Phase 1 - Definition
* * * * *
[Add new 8-6.1.5 and 8-6.1.6 to
read as follows:]
8-6.1.5 Document High-Level
Architecture
A high-level architectural diagram
(e.g., hardware, communications, security devices, and interconnected
resources) is developed for all applications. The architectural diagram
is submitted to the manager, SIS, for review and determination of the
impact on the infrastructure and the need for additional security controls
for the application (e.g., enclave).
8-6.1.6 Document Information
Resources in the Enterprise Information Repository
All applications are documented in
the Enterprise Information Repository (EIR).
8-6.2 Phase 2 - Design and
Integration
* * * * *
[Delete 8-6.2.1, Document High-Level
Architecture, and 8-6.2.2, Document Information Resources in the Enterprise
Information Repository.]
* * * * *
[Delete 8-6.2.11, Conduct Vulnerability
Scan.]
* * * * *
[Renumber current 8-6.2.3 through
8-6.2.16 as new 8-6.2.1 through 8-6.2.13. Add new 8-6.2.14 to read as
follows:]
8-6.2.14 Register Application
in eAccess
The application is registered in eAccess
which is the Postal Service application for managing the authorization
process for personnel needing to access the application and the associated
information. Registration is also required for the use of managed accounts
(i.e., machine accounts, etc.).
8-6.3 Phase 3 - Testing
* * * * *
[Renumber current 8-6.3.4 through
8-6.3.9 as new 8-6.3.5 through 8-6.3.10. Add new 8-6.3.4 to read as follows:]
8-6.3.4 Conduct Vulnerability
Scan
A vulnerability scan is recommended
for all information resources and applications, and is required for some
information resources and applications (see Handbook AS-805-A, Application
Information Security Assurance [ISA] Process).
* * * * *
10 Hardware and Software Security
* * * * *
10-2 Roles and Responsibilities
* * * * *
10-2.8 Database Administrators
Database administrators (DBAs) are
responsible for:
* * * * *
[Revise item d to read as follows:]
d. Tracking hardware and
software vulnerabilities, and deploying database security patches.
* * * * *
10-4 Configuration and Change
Management
* * * * *
[Renumber current 10-4.5 through
10-4.6 as new 10-4.6 through 10-4.7. Add new 10-4.5 to read as follows:]
10-4.5 Patch Management
An effective patch management process
must be implemented to investigate, prioritize, test, track, and control
the deployment and maintenance of software releases, and to resolve known
security vulnerabilities. The patch management process must be addressed
by all information resources installed in the Postal Computing Environment.
Personnel involved in the patch management process must be trained to
ensure a viable vulnerability mediation process.
Patch management involves acquiring,
testing, and installing multiple patches (code changes) to software systems,
including operating system software, supporting software and packages,
firmware, and application software. Patch management tasks include: maintaining
current knowledge of available patches; deciding what patches are appropriate
for particular information resources; prioritizing the
patches to be installed; testing patches
in a nonproduction environment first in order to check for unwanted or
unforeseen side effects; developing a backout plan, which includes backing
up the systems about to be patched to be sure that it is possible to return
to a known-good working configuration should something go wrong with the
patch; ensuring that patches are installed properly; testing information
resources after installation; and documenting all associated procedures,
such as specific configurations required.
Patch management is critical to ensure
the integrity and reliability of information resources. Patch management
should be capable of:
a. Highly granular patch
update and installation administration (i.e., treating patches and mainframes,
servers, desktops, and laptops separately).
b. Tracking machines, and
updating and enforcing patches centrally.
c. Verifying successful
deployment on each machine.
d. Deploying client settings,
service packs, patches, hot fixes, and similar items network-wide in a
timely manner in order to address immediate threats.
e. Initiating from a central
management console.
f. Providing scheduling,
desktop management, and standardization tools to reduce the costs associated
with distribution and management.
g. Providing ongoing deployment
for both new and legacy systems in mixed hardware and OS environments.
h. Automating the repetitive
activity associated with rolling out patches.
i. Analyzing the operating
system and applications to identify possible security holes.
j. Scanning the entire
network (IP address by IP address) and providing information such as service
pack level of the machine, missing security patches, key registry entries,
weak passwords, users and groups, and more.
k. Analyzing scan results
using filters and reports to proactively secure information resources
(e.g., installing service packs and hotfixes, etc.).
* * * * *
Appendix A Consolidated Roles
and Responsibilities
* * * * *
11
Portfolio Managers
Portfolio managers are responsible
for the following:
* * * * *
[Reletter current items e through
i as new items f through j. Add new item e to read as follows:]
e. If a documented vulnerability
will not be mitigated, preparing and signing an acceptance of responsibility
letter as part of the ISA process.
* * * * *
35 Database Administrators
Database administrators are responsible
for the following:
* * * * *
[Revise item l to read as follows:]
l. Tracking hardware and
software vulnerabilities, and deploying database security patches.
* * * * *
36 All Personnel
* * * * *
[Reletter current items e through
s as new items g through u. Add new items e and f to read as follows:]
e. Always using their physical
and technology electromechanical access control identification badge or
device to gain entrance to a controlled area.
f. Ensuring no one tailgates
into a controlled area on their badge.
* * * * *
Appendix B Information Security
and Related Documents
[Revise Appendix B to read as follows:]
Administrative Support Manual (ASM)
Subchapter 27, Security
Subchapter 28, Emergency Preparedness
Chapter 8, Information Resources
Handbooks
AS-805, Information Security
AS-805-A, Application Information
Security Assurance (ISA) Process
AS-805-B, Infrastructure Information
Security Assurance (ISA) Process
AS-805-C, Information Security
for General Users
AS-805-D, Information Security
Network Connectivity Process
AS-805-G, Information Security
for Mail Processing/Mail Handling Equipment
AS-816, Open VMS Security
AS-353, Guide to Privacy and the
Freedom of Information Act
Other Related Documents
Enterprise Information Security
Architecture
USPS PKI Certificate Policy (CP)
USPS CA Certificate Practice Statement
(CPS)
Boilerplate
for Contracts and Agreements
Guidelines for New Development of
Web-based Applications
Guide to Coding Secure Software
Information Security Code Review Standards
COTS Software Security Evaluation
Process
Pub. 805-A, Information Security
Assurance (ISA) Process
Pub.
805-E, What Every Employee Needs to Know About Information
Security
PS Form 1357, Request for Computer
Access
PS Form 1360, Information Security
Incident Report
MOP
IT-03-11-2002, Computer Use
* * * * *
— Corporate Information
Security,
Information Technology, 9-29-05
HANDBOOK AS-805-A REVISION
Application Information Security Assurance
(ISA) Process
Effective September 29, 2005, we are
revising Handbook AS-805-A, Application Information Security Assurance
(ISA) Process, to address the registering of applications in eAccess
and the acceptance of responsibility letter for documented vulnerabilities
that will not be mitigated.
We will incorporate these revisions
into the next online version of Handbook AS-805-A accessible on the Postal
ServiceTM PolicyNet Web site:
• Go to http://blue.usps.gov.
• Under "Essential Links"
in the left-hand column, click on References.
• Under "References"
in the right-hand column, under "Policies," click on PolicyNet.
• Then click on HBKs.
(The direct URL for the Postal Service
PolicyNet Web site is http://blue.usps.gov/cpim.)
Handbook AS-805-A, Application Information Security
Assurance (ISA) Process
* * * * *
2 Roles and Responsibilities
* * * * *
2-6 Portfolio Managers
Portfolio managers are responsible
for the following:
* * * * *
[Reletter current e as new h. Add
new items e, f, and g to read as follows:]
e. Preparing and signing
an acceptance of responsibility letter, if a documented vulnerability
will not be mitigated.
f. Ensuring that the application
is registered in eAccess.
g. Accepting all risks,
liabilities, and responsibilities and assuming personal accountability
for any damage to the Postal Service (including direct financial losses
and any costs resulting from remedial actions in operating the application)
for authorizing an application to enter the production environment prior
to completing the application ISA process.
* * * * *
4 The ISA Process
* * * * *
4-1 Phase 1 - Definition
* * * * *
4-1.5 Next Steps
* * * * *
[Swap sections 4-1.5.2 and 4-1.5.3
as follows: 4-1.5.2, Applications Designated as Legacy and 4-1.5.3, All
Other Applications.]
* * * * *
4-2 Phase 2 - Design and Integration
* * * * *
4-2.4 Activities
* * * * *
[Renumber current 4-2.4.9 through
4-2.4.10 as new 4-2.4.12 through 4-2.4.13. Add new 4-2.4.9 through 4-2.4.11
to read as follows:]
4-2.4.9 Incorporate Security
Requirements in Service Level Agreements and Trading Partner Agreements
Service level agreements (SLAs) are
developed for all applications. Trading partner agreements (TPAs) are
developed for all externally managed and/or developed applications. Information
security requirements are addressed in all SLAs and TPAs.
4-2.4.10 Develop Operational
Security Training
Appropriate materials are developed
for training users, system administrators, managers, and other personnel
on the correct use of the application and its security controls.
4-2.4.11 Register Application
in eAccess
The application is registered in eAccess,
which is the Postal Service's application for managing the authorization
process for personnel needing to access an application and the associated
information. Registration is also required for the use of managed accounts
(i.e., machine accounts, etc.).
4-3 Phase 3 - Testing
* * * * *
[Delete section 4-3.4.5, Harden
Platform.]
* * * * *
4-4 Phase 4 - Evaluation
* * * * *
4-4.3 Roles and Responsibilities
[Change the Portfolio manager and
Accreditor (manager, CISO) roles and responsibilities to read as follows:]
| Portfolio manager
|
Analyzes ISA and
business documentation, makes the decision to escalate security concerns
or prepares a risk mitigation plan addressing high and medium risks
and recommending whether the risks should be accepted, transferred,
or further mitigated. If a documented vulnerability will not be mitigated,
prepares and signs an acceptance of responsibility letter and forwards
it (the risk mitigation plan and ISA documentation package) to the
accreditor. |
| Accreditor (manager,
CISO) |
Analyzes ISA and
business documentation, makes the decision to escalate security concerns,
or prepares and signs an accreditation letter. Forwards the accreditation
letter and ISA documentation package to the executive sponsor and
portfolio manager. |
* * * * *
4-4.4 Activities
* * * * *
[Revise title and text of 4-4.4.5
to read as follows:]
4-4.4.5 Escalate Security Concerns
or Prepare Risk Mitigation Plan and Acceptance of Responsibility Letter
(if Required)
The portfolio manager reviews the certification
letter, the supporting ISA, and the business documentation, and escalates
security concerns or prepares a risk mitigation plan for any residual
risks rated as medium or high. The portfolio manager then recommends whether
the risks should be accepted, transferred, or further mitigated. If a
documented vulnerability will not be mitigated, the portfolio manager
prepares and signs an acceptance of responsibility letter and then forwards
it, the risk mitigation plan, and ISA documentation package to the accreditor.
* * * * *
Exhibit 4a ISA Templates
[Add a row to Exhibit 4a after
the Risk Mitigation Plan row to read as follows:]
| Template
Name |
Applicability
|
Purpose
|
| Acceptance of Responsibility
for Documented Vulnerability Letter |
For a documented
vulnerability that will not be mitigated. |
For the portfolio
manager to accept responsibility for a documented vulnerability that
will not be mitigated. |
Exhibit 2
Relationship of ISA Roles
[Revise Exhibit 2 as follows:]
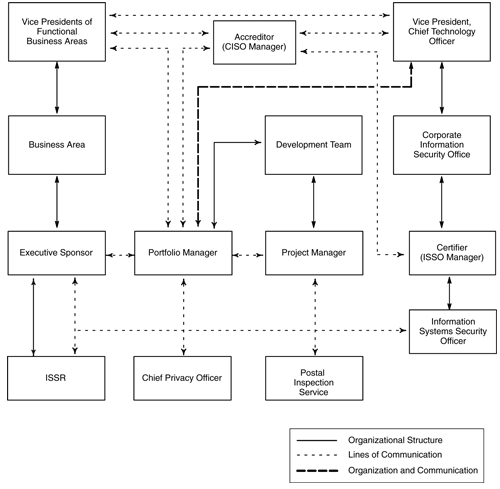
Exhibit 4-4
Phase 4, Evaluation
[Revise Exhibit 4-4 as follows:]
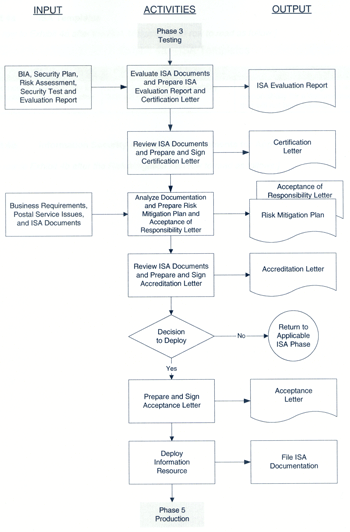
* * * * *
Exhibit 4b
Information Security Assurance
Requirements for Applications
[Add a row to Exhibit 4b after
the Risk Mitigation Plan row to read as follows:]
| ISA
Phase |
ISA
Deliverable |
New
Applications |
Legacy* |
Small Applications |
Field Application |
| Nonsensitive
& Noncritical |
Business
Controlled |
Sensitive
& Critical |
| Deliver-
ables |
Respon-
sible |
Deliver-
ables |
Respon-
sible |
Deliver-
ables |
Respon-
sible |
Deliver-
ables |
Respon-
sible |
Deliver-
ables |
Respon-
sible |
Deliver-
ables |
Respon-
sible |
| 4
|
Acceptance
of Responsibility for a Documented Vulnerability Letter |
blank |
blank |
YES
for documented vulnerability that will not be mitigated |
Portfolio
Mgr |
YES
for documented vulnerability that will not be mitigated |
Portfolio
Mgr |
blank |
blank |
YES
for documented vulnerability that will not be mitigated |
Portfolio
Mgr |
blank |
blank |
* * * * *
— Corporate Information Security, Information Technology, 9-29-05
|
